Discover Innovative Security with BQT Solutions for All Your Requirements
Discover Innovative Security with BQT Solutions for All Your Requirements
Blog Article
Maximizing Company Security: The Ultimate Overview to Electronic Security Solutions
In the fast-paced and ever-evolving landscape of company protection, the dependence on electronic safety and security remedies has actually come to be extremely important for securing beneficial properties, confidential info, and preserving operational connection. In this overview to digital security solutions, we will check out the most recent fads, cutting-edge technologies, and ideal techniques to strengthen your business against potential threats and susceptabilities.
Relevance of Electronic Protection Solutions
When considering the protection of possessions and sensitive details, the importance of digital protection services can not be overstated. In today's interconnected globe, where cyber hazards are frequently advancing and coming to be extra innovative, organizations must prioritize applying durable digital protection actions to safeguard their information and operations. Electronic security options encompass a vast array of modern technologies and practices developed to resist unauthorized gain access to, information violations, malware, and other cyber risks.
Among the key benefits of digital safety solutions is their capability to provide real-time surveillance and threat detection. BQT Solutions. With tools like breach detection systems, firewall softwares, and protection information and occasion management (SIEM) systems, companies can proactively recognize and react to protection occurrences prior to they escalate right into major breaches. Additionally, electronic safety options assist make certain conformity with sector laws and criteria, protecting businesses from prospective lawful and economic effects
Sorts Of Electronic Safety And Security Solutions
Provided the essential relevance of electronic safety and security solutions in safeguarding businesses against cyber hazards, it is important to explore the various kinds of digital protection systems available to boost defense and durability. One of one of the most usual sorts of digital safety systems is the firewall software, which functions as a barrier between a company's internal network and exterior networks, filtering system out potentially hazardous data. Invasion Discovery Solution (IDS) are likewise important, as they monitor network website traffic for questionable activity and sharp managers to potential threats. In addition, organizations typically depend on file encryption modern technologies to secure sensitive information both at remainder and in transit. Access control systems, including biometric visitors and keycard accessibility, help control access to physical spaces and shield her explanation assets. Video clip monitoring systems play a role in tracking and recording tasks within and around the properties. By using a mix of these digital protection systems, organizations can establish a robust protection against various safety risks.
Applying Access Control Procedures

Furthermore, access control procedures can be integrated with monitoring systems to monitor and tape individuals' motions within secured areas. This assimilation improves security by supplying an extensive summary of that is accessing particular areas at any type of given time. Gain access to control systems can be configured to restrict access based on time, location, or specific credentials, permitting organizations to customize security procedures according to their certain demands.
Cybersecurity Ideal Practices
To improve overall safety position, applying robust cybersecurity ideal techniques is important in safeguarding electronic properties and information honesty. Conducting routine safety audits and analyses aids identify weaknesses and locations for renovation.
Developing a thorough case reaction strategy makes it possible for find more information swift and efficient feedbacks to safety violations, reducing possible damages. Implementing access controls based on the principle of the very least privilege limits the exposure of essential systems and info to just those who need it for their functions. By including these ideal practices right into cybersecurity strategies, businesses can strengthen their defenses versus progressing cyber risks.
Surveillance and Monitoring Solutions
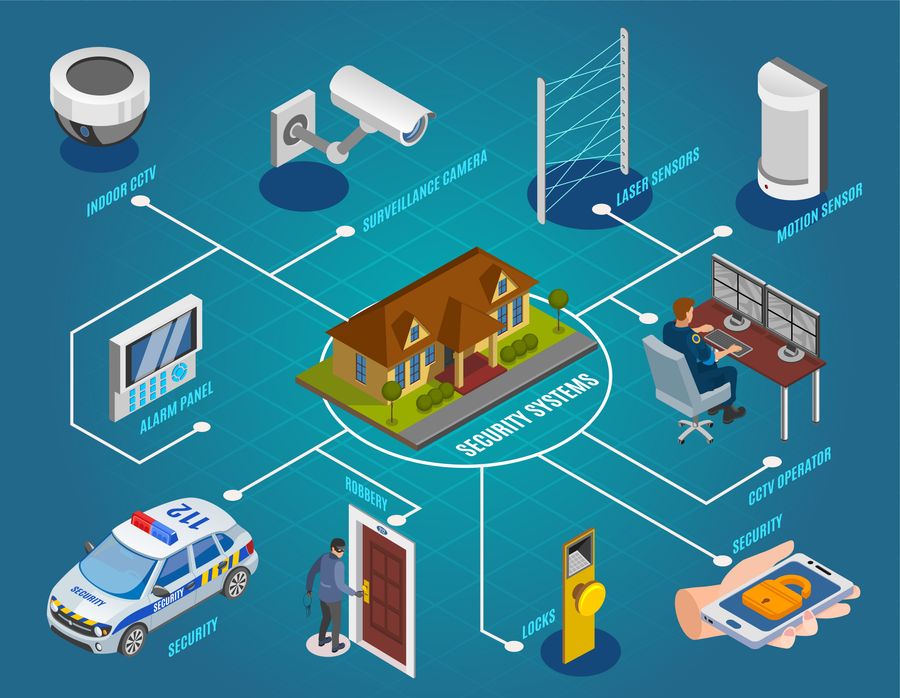
Video monitoring solutions use remote monitoring abilities, allowing licensed employees to watch on the facilities even when off-site. Furthermore, progressed functions like activity detection, face recognition, and certificate plate recognition boost the general security pose of the organization. Incorporating monitoring systems with alarm systems and gain access to control further strengthens the security framework, allowing a proactive response to possible protection breaches.
Conclusion
Finally, digital protection remedies are necessary for making best use of organization security. By implementing access control measures, cybersecurity finest practices, and monitoring and monitoring services, organizations can efficiently secure their assets and info. It is essential to purchase the best digital security systems to make sure the safety and safety of the company. Keep in mind, prevention is crucial in securing versus prospective threats and susceptabilities (BQT Electronic Security).
Report this page